Technical Working Group on Biological Evidence Preservation. Federal Agency in the national security space providing cybersecurity digital forensics and incident response for classified and unclassified networks.
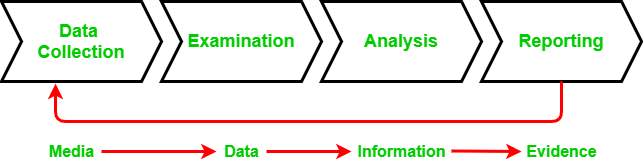
Chain Of Custody Digital Forensics Geeksforgeeks
It was at all times in the custody of a person designated to handle it and for which it was never unaccounted.
. It is a must to assure the court of law that the evidence is authentic ie it is the same evidence seized at the crime scene. A process and record that shows who obtained the evidence. This form is to be used when collecting a hardware device containing data that may be of interest in a case.
The collecting individuals name. A typical Chain of Custody Form will describe the evidence and detail the location and conditions under which the evidence was collected. Chain of Custody refers to the logical sequence that records the sequence of custody control transfer analysis and disposition of physical or electronic evidence in legal cases.
Where and when the evidence was obtained. Some of these documents were used within an ASCLDLAB accredited laboratory operating to ISO 17025 standards and others have been used within a US. Quantity description of property include make model serial number condition how secured etc property.
Chain of Custody Form. A chain-of-evidence form which is used to document what has and had not been done with the original evidence and forensic copies of the evidence is also known as an. A simple way to record a documents provenance is with a chain of custody form that an individual fills out with information such as.
In the event that lab results are challenged a chain of custody form can prove the specimen was handled according to the federally mandated chain of custody and control procedures. Every treatment center counseling service and medical facility that performs a specimen collection. Date time m.
Best Practices for Evidence Handlers. The Biological Evidence Preservation Handbook. Document helps to ensure that the integrity of the sample is preserved from collection to analysis to destruction or further transport.
Evidence custody form d. The Biological Evidence Preservation Handbook. EVIDENCE SUBVOUCHER- A chain of custody form used as a subvoucher accompanies evidence to record any changes of custody that may occur while the evidence leaves the evidence room.
For the Safe Handling of Contaminated Document Evidence and the Preservation of Associated Trace Evidence. The sequencing of the chain of evidence follows this order. Name grade and title of person from whom received quantity.
Although it is a lengthy process it is required for. The location from which it was retrieved. Received by purpose of change.
One group of actions is separated from another based on the level of authority required to execute them. A description of the document. DEFINITIONS Chain of Custody COC a written legal document used to track the transfer of a samples from person to person.
Evidence custody form d. The purpose of this template is to document information on who are the releasing officer and receiver of the seized evidence. A chain of custody form is a multi-part document used to provide evidence of proper specimen handling during the drug testing process.
The chain of custody is the most critical process of evidence documentation. Chain-of-custody forms are used to keep track of who touches each piece of evidence from the time collected to the time it goes to trial. In the event that lab results are challenged a chain of custody form can prove the specimen was handled according to the federally mandated chain of custody and control procedures.
Each step in the chain is essential as if broke the evidence may be rendered inadmissible. All lab personnel should become very familiar with this SOP. Thus we can say that preserving the chain of custody is about following the correct and.
Property owner unknown. Best Practices for Evidence Handlers. A chain-of-evidence form which is used to document what has and had not been done with the original evidence and forensic copies of the evidence is also known as an.
Crd reportcid roi. Who secured the evidence. Use a copy of the original evidence voucher or make an extract of the original.
Da form 4137 1 jul 1976. Always prepare subvouchers in duplicate with the original accompanying the evidence. A chain of custody form is a multi-part document used to provide evidence of proper specimen handling during the drug testing process.
And other documents which form the. Present property owner. A Chain of Custody Evidence Log is a document that is used to record all necessary information in terms of collecting and taking custody of the seized items.
The Chain of Custody Form CCF or CoC is used to record all changes in the seizure custody control transfer analysis and disposition of physical and electronic evidence. A chain of custody form is a multi-part document used to provide evidence of proper specimen handling during the drug testing process. The Chain-of-Evidence Model illustrates the discrete sets of actions carried out by an insider attempting to inflict malicious damage in an intranet environment.
Do you believe evidence collected at a crime scene that proves beyond doubt that a person is a serial killer should be excluded if one officer failed to sign the chain of custody forms while handling the evidence. Department of Commerce National Institute of Standards and Technology. Chain of evidence form.
The name of the document or file. Location where property was obtaineed purpose for which property was obtained. And who had control or possession of the evidence.
GuidelinesEnsure that this form only refers to one item of evidence and that one is completed for each item of evidenceThis form must be accompanied by Chain of Custody forms which detail the individuals that have handled the evidence. Originally required only by the federal government the Federal Workplace Drug Testing Program is now commonplace in the private sector as well. Item Control and Chain of Custody.
A chaindocx - A chain-of-evidence form which is used to document what has and has not been done with the original evidence and forensic copies of the.

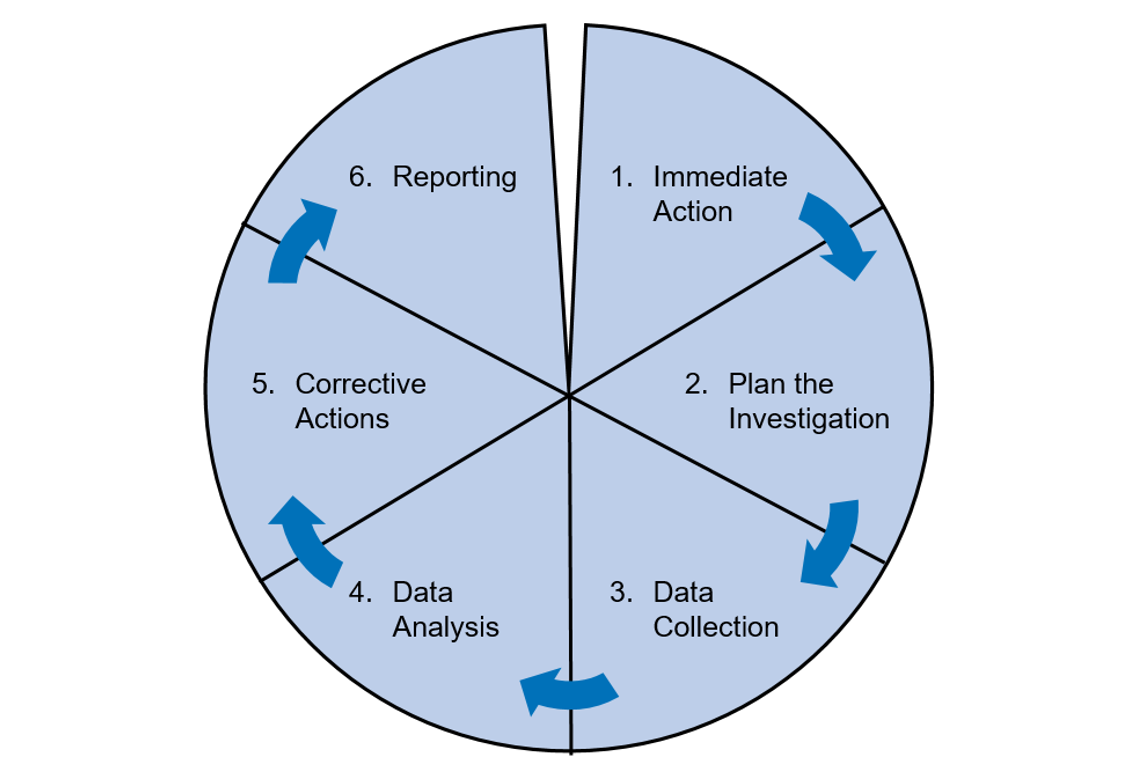
Six Steps For Successful Incident Investigation Risktec

Chain Of Custody And Why It Is Important In A Criminal Case Ladyjustice Speaks

Iso Iec 27043 2015 En Information Technology Security Techniques Incident Investigation Principles And Processes
0 Comments